[av_textblock size=” font_color=” color=”]
Web Application Firewall (WAF) na GoCache – Proteção para seu site de forma simples e eficiente
A GoCache tem a missão de tornar a internet mais rápida, segura e disponível, e nosso mais recentemente lançamento, o Web Application Firewall (WAF) é um passo importante rumo a este objetivo. Aqui entramos em mais detalhe no uso do WAF na GoCache.
Com interface administrativa completa e simplificada, o WAF da GoCache já está disponível para todos os planos.
Nossos clientes já vinham utilizando o WAF nas últimas semanas, ajudando com o “beta” e fornecendo valioso feedback. Agora o produto está maduro o suficiente para ser lançado no mercado.
Inicialmente liberado para uso em todos os planos sem custo adicional, o WAF ajuda a proteger contra alguns dos ataques mais comuns e prejudiciais na web, como SQL Injection e Cross Site Scripting (XSS).
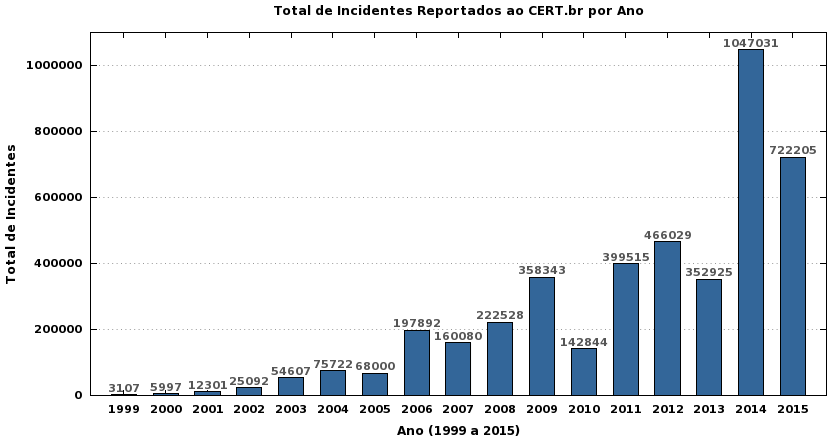
Para referência, de todos os incidentes reportados ao CERT durante o ano de 2015, 9,09% foram do tipo “web”.
Ao levarmos em conta a escalada na quantidade de incidentes de segurança reportados anualmente, fica fácil entender a importância deste tipo de mecanismo de proteção.
É necessário frisar também que a vasta maioria dos incidentes sequer é reportada ao CERT, ou seja, o volume de ataques é bem maior do que o registrado no gráfico.
Como funciona o WAF na GoCache?
Em seu Painel de Controle na GoCache, acesse a opção “Segurança”:
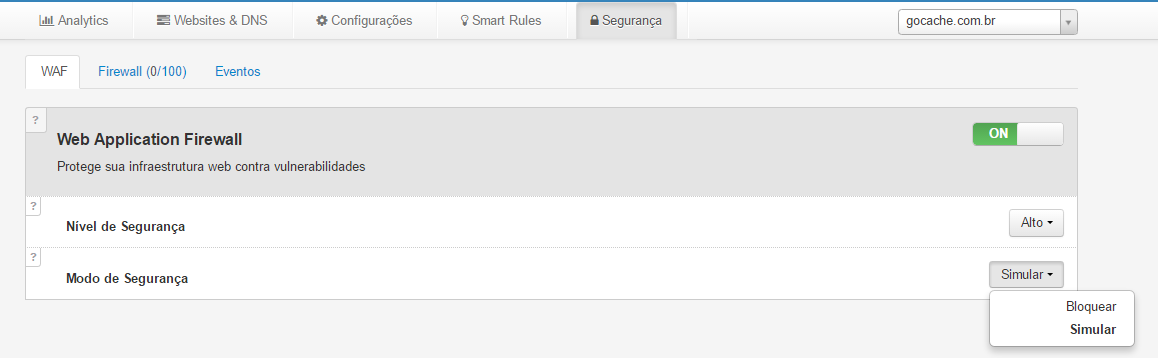
Você verá então a primeira tela, onde pode ligar/desligar o WAF e escolher o nível de segurança pré-configurado na ferramenta – Baixo, Médio ou Alto.
Você verá também a opção de uso – Bloquear ou Simular, conforme a tela abaixo:
Aconselhamos o uso da opção “Simular” inicialmente, pois assim você pode configurar o nível de segurança “alto” e adicionar outras regras sem que os bloqueios sejam efetivados, até ter certeza de estar bloqueando somente o tráfego indesejado.
Você pode acompanhar o que seria bloqueado (ou o que foi bloqueado caso ative o modo de segurança “bloquear”) no Log de Eventos:
E ao clicar no ícone “Detalhes”:
você pode ver qual foi a ação, a URL e o motivo do bloqueio:
Você também tem a opção de configurar Whitelist e Blacklist diretamente no Firewall:
É possível configurar o bloqueio/liberação utilizando como critério o IP/Range de IP, País, Continente, User Agent, Referer Host ou URI.
A ferramenta é completa e a interface de uso bastante intuitiva, quer testar sem compromisso? Clique aqui e faça nosso trial de 7 dias, não precisa de cartão de crédito!
Go faster. GoCache.
[/av_textblock]